With the passage of time, the concern about users visiting institutions, companies, or any other business unit has increased dramatically. In light of the current security situation, it is critical for everyone to keep track of who visits them.
Traditionally, most companies, units, or institutions use logbooks to keep track of visitors and record information such as name, time, and purpose. However, it has been observed that most of the time, these logbooks are kept purely for formal purposes, with no cross-checking or oversight. Later, whenever an unpleasant incident occurs, we begin to blame ourselves for the lack of accuracy, incorrect data management, and log bookkeeping. Even if the data records are available, searching for or finding a specific record amid enormous amounts of data is a time-consuming and inefficient procedure.
This necessitates a method or solution that will not only assist us in correctly maintaining data, but also hold the system accountable for security concerns in the event of an occurrence. RationalTabs has conducted extensive research and development in a variety of industries in order to build a solution that is best suited for visitor records administration in a security-conscious environment.
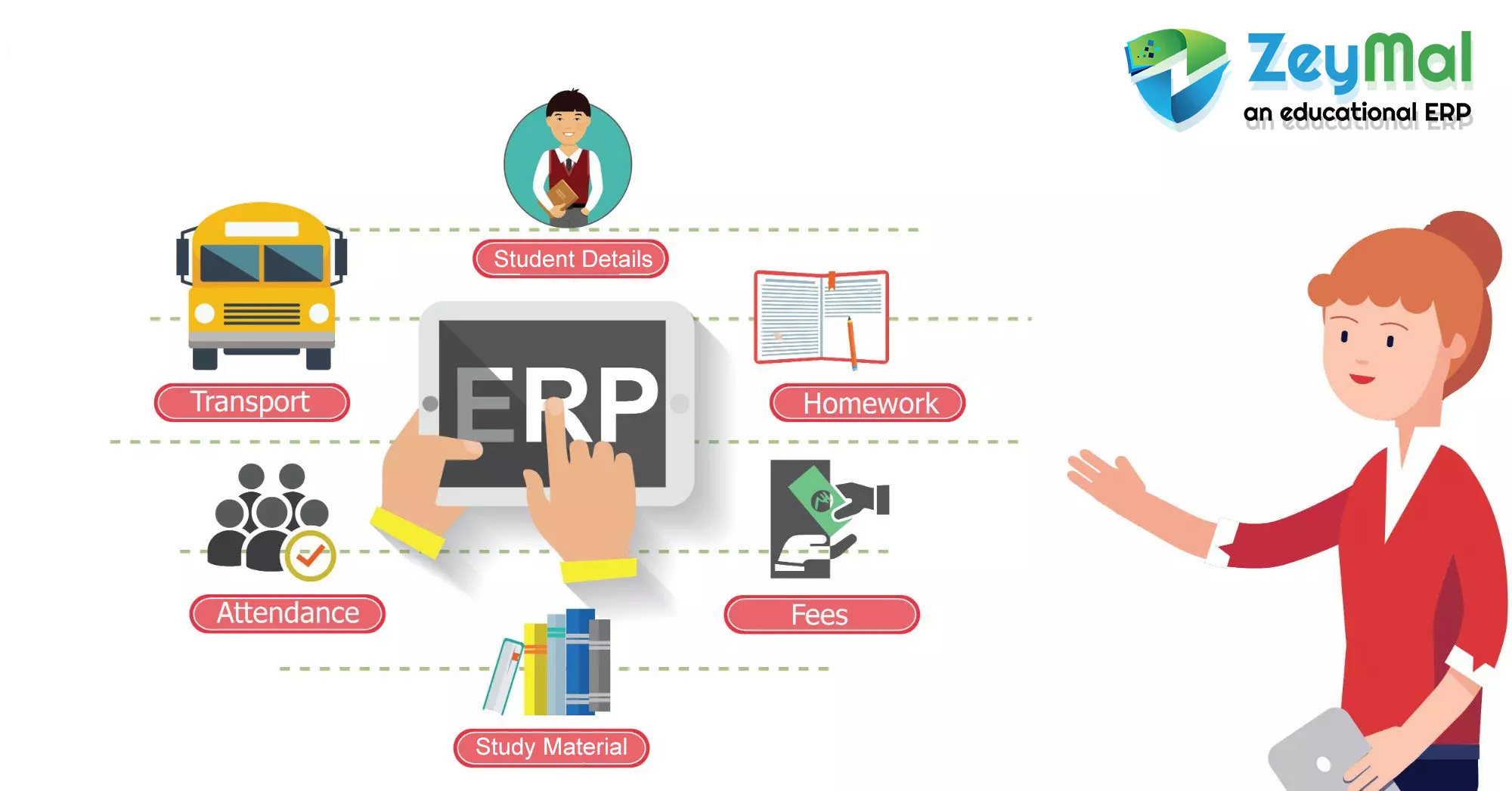
Our visitor management system is extremely adaptable to many business and organizational sectors. We can save information such as the identity of the visitor, the purpose of the visit, the authority or authorized person, the time in-out, vehicle information, accompanying persons, materials carried, and so on in our solution. Add-ons such as an embedded camera for photo-taking can be incorporated based on customer requirements. Based on these inputs, visitor pass slips can be generated, which will include all of the necessary information as well as a photograph, expediting the entire process.
We also have the ability to integrate various hardware solutions for additional functionalities, resulting in a more sophisticated and secure system. These hardware connections work in tandem with our ERP systems and don't require any additional software or tools. Fingerprint biometrics, LF, HF, or UHF RFID technology, facial recognition or detection, boom barriers, flap barriers, turnstiles, door access controls, and other solutions are among the technologies that have been integrated.
These solutions, depending on their capabilities, assist us in controlling access to visitors based on their allowed permits to various portions of buildings, capturing fingerprints, and restricting user access to specific locations, as well as restricting vehicles to specific points. Overall, these new technologies provide consumers the freedom to select solutions that meet their specific objectives and security requirements.